
PDF) An Application of Integrating Role and Lattice Based Access Control in Database Engineering | Isabella Kotini - Academia.edu

Hasse diagram for an example lattice-based access control (LBAC) policy... | Download Scientific Diagram

A security lattice (left-hand side) and its presentation by a graph... | Download Scientific Diagram

access control - BLP Lattice structure with missing top and bottom levels - Information Security Stack Exchange

Security Models Pt. 2 - State Machine, Lattice-based information flow (CISSP Free by Skillset.com) - YouTube

![PDF] Lattice-based access control models | Semantic Scholar PDF] Lattice-based access control models | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/9a0174d303de6edb48be5fefdc3ddffa0d09b029/8-Figure5-1.png)
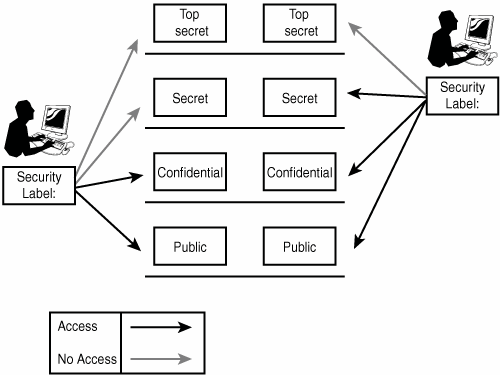
![PDF] Lattice-based access control models | Semantic Scholar PDF] Lattice-based access control models | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/9a0174d303de6edb48be5fefdc3ddffa0d09b029/2-Figure1-1.png)
![PDF] Lattice-based access control models | Semantic Scholar PDF] Lattice-based access control models | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/9a0174d303de6edb48be5fefdc3ddffa0d09b029/5-Figure3-1.png)
![PDF] Lattice-based access control models | Semantic Scholar PDF] Lattice-based access control models | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/9a0174d303de6edb48be5fefdc3ddffa0d09b029/10-Figure7-1.png)


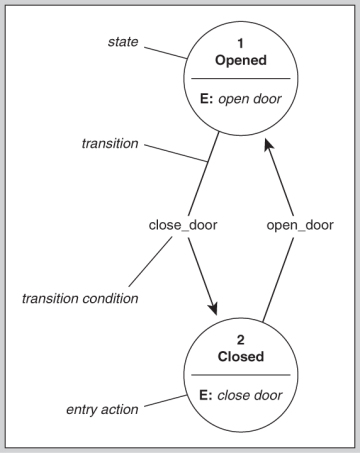
![PDF] Lattice-based access control models | Semantic Scholar PDF] Lattice-based access control models | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/9a0174d303de6edb48be5fefdc3ddffa0d09b029/8-Figure4-1.png)
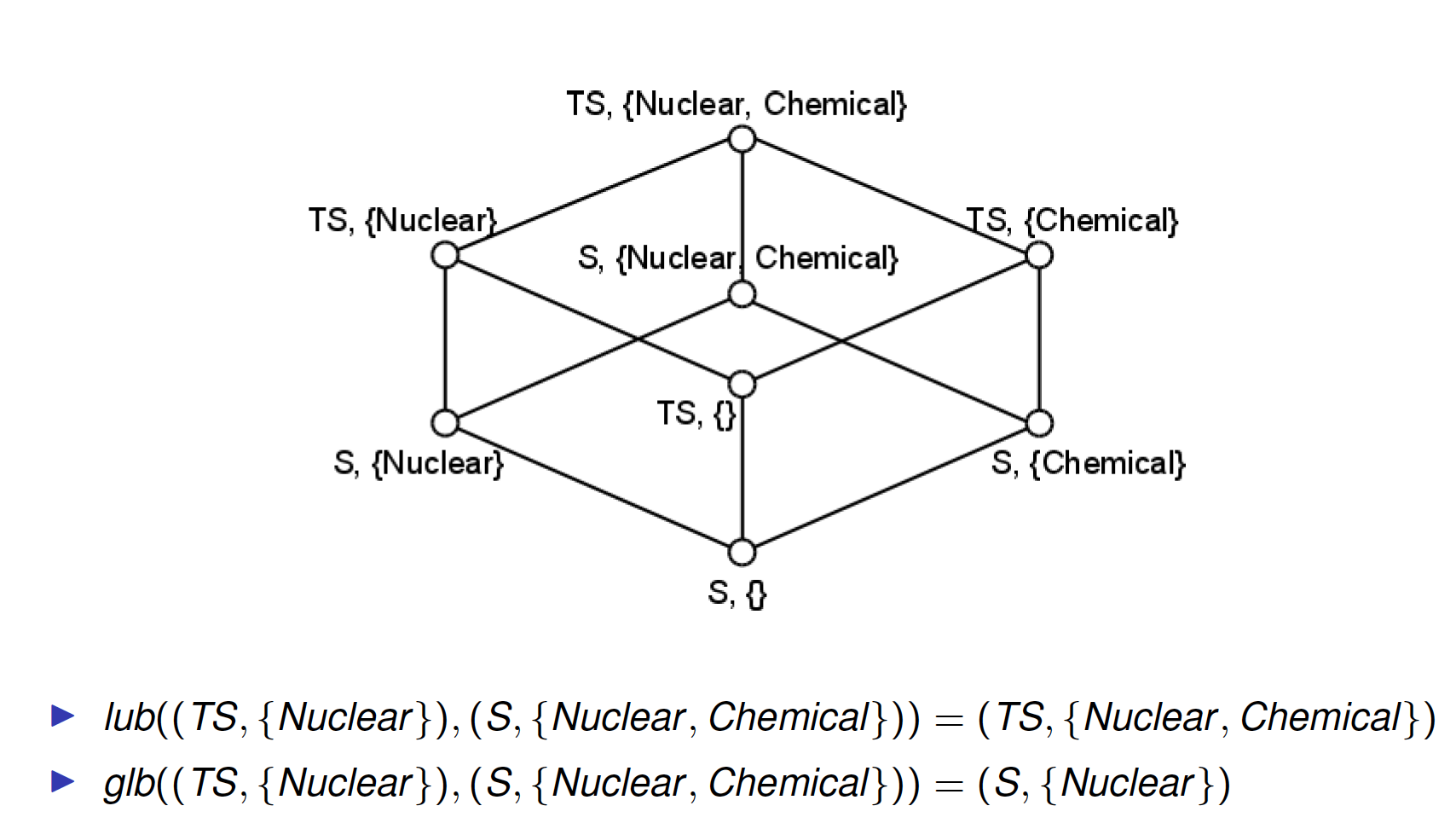



![PDF] Lattice-based access control models | Semantic Scholar PDF] Lattice-based access control models | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/9a0174d303de6edb48be5fefdc3ddffa0d09b029/4-Figure2-1.png)
